Review:
A Master of Djinn, by P. Dj l Clark
| Series: |
Dead Djinn Universe #1 |
| Publisher: |
Tordotcom |
| Copyright: |
2021 |
| ISBN: |
1-250-26767-6 |
| Format: |
Kindle |
| Pages: |
391 |
A Master of Djinn is the first novel in the Dead Djinn Universe,
but (as you might guess from the series title) is a direct sequel to the
novelette
"A Dead Djinn in Cairo". The
novelette is not as good as the novel, but I recommend reading it first
for the character introductions and some plot elements that carry over.
Reading
The Haunting of Tram Car 015
first is entirely optional.
In 1912 in a mansion in Giza, a secret society of (mostly) British men is
meeting. The Hermetic Brotherhood of Al-Jahiz is devoted to unlocking the
mysteries of the Soudanese mystic al-Jahiz. In our world, these men would
likely be colonialist plunderers. In this world, they still aspire to
that role, but they're playing catch-up. Al-Jahiz bored into the Kaf,
releasing djinn and magic into the world and making Egypt a world power in
its own right. Now, its cities are full of clockwork marvels, djinn walk
the streets as citizens, and British rule has been ejected from India and
Africa by local magic. This group of still-rich romantics and crackpots
hopes to discover the knowledge lost when al-Jahiz disappeared. They have
not had much success.
This will not save their lives.
Fatma el-Sha'arawi is a special investigator for the Ministry of Alchemy,
Enchantments, and Supernatural Entities. Her job is sorting out the
problems caused by this new magic, such as a couple of young thieves with
a bottle full of sleeping djinn whose angry reaction to being unexpectedly
woken has very little to do with wishes. She is one of the few female
investigators in a ministry that is slowly modernizing with the rest of
society (Egyptian women just got the vote). She's also the one called to
investigate the murder of a secret society of British men and a couple of
Cairenes by a black-robed man in a golden mask.
The black-robed man claims to be al-Jahiz returned, and proves to be
terrifyingly adept at manipulating crowds and sparking popular dissent.
Fatma and the Ministry's first attempt to handle him is a poorly-judged
confrontation stymied by hostile crowds, the man's duplicating bodyguard,
and his own fighting ability. From there, it's a race between Fatma's
pursuit of linear clues and the black-robed man's efforts to destabilize
society.
This, like the previous short stories, is a police procedural, but it has
considerably more room to breathe at novel length. That serves it well,
since as with "A Dead Djinn in Cairo" the procedural part is a linear,
reactive vehicle for plot exposition. I was more invested in Fatma's
relationships with the supporting characters. Since the previous story,
she's struck up a romance with Siti, a highly competent follower of the
old Egyptian gods (Hathor in particular) and my favorite character in the
book. She's also been assigned a new partner, Hadia, a new graduate and
another female agent. The slow defeat of Fatma's irritation at not being
allowed to work alone by Hadia's cheerful competence and persistence (and
willingness to do paperwork) adds a lot to the characterization.
The setting felt a bit less atmospheric than
The Haunting of Tram
Car 015, but we get more details of international politics, and they're a
delight. Clark takes obvious (and warranted) glee in showing how the
reintroduction of magic has shifted the balance of power away from the
colonial empires. Cairo is a bustling steampunk metropolis and capital of
a world power, welcoming envoys from West African kingdoms alongside the
(still racist and obnoxious but now much less powerful) British and other
Europeans. European countries were forced to search their own mythology
for possible sources of magic power, which leads to the hilarious scene of
the German Kaiser carrying a sleepy goblin on his shoulder to monitor his
diplomacy.
The magic of the story was less successful for me, although still
enjoyable. The angels from "A Dead Djinn in Cairo" make another
appearance and again felt like the freshest bit of world-building, but we
don't find out much more about them. I liked the djinn and their
widely-varied types and magic, but apart from them and a few glimpses of
Egypt's older gods, that was the extent of the underlying structure.
There is a significant magical artifact, but the characters are
essentially handed an instruction manual, use it according to its
instructions, and it then does what it was documented to do. It was a bit
unsatisfying. I'm the type of fantasy reader who always wants to read the
sourcebook for the magic system, but this is not that sort of a book.
Instead, it's the kind of book where the investigator steadily follows a
linear trail of clues and leads until they reach the final confrontation.
Here, the confrontation felt remarkably like cut scenes from a Japanese
RPG: sudden vast changes in scale, clockwork constructs, massive monsters,
villains standing on mobile platforms, and surprise combat reversals. I
could almost hear the fight music and see the dialog boxes pop up. This
isn't exactly a complaint I love Japanese RPGs but it did add to the
feeling that the plot was on rails and didn't require many decisions from
the protagonist. Clark also relies on an overused plot cliche in the
climactic battle, which was a minor disappointment.
A Master of Djinn won the Nebula for best 2021 novel, I suspect
largely on the basis of its setting and refreshingly non-European magical
system. I don't entirely agree; the writing is still a bit clunky, with
unnecessary sentences and stock phrases showing up here and there, and I
think it suffers from the typical deficiencies of SFF writers writing
mysteries or police procedurals without the plot sophistication normally
found in that genre. But this is good stuff for a first novel, with fun
supporting characters (loved the librarian) and some great world-building.
I would happily read more in this universe.
Rating: 7 out of 10
 I hope you had a nice Halloween!
I've collected together some songs that I've enjoyed over the last couple of
years that loosely fit a theme: ambient, instrumental, experimental, industrial,
dark, disconcerting, etc. I've prepared a Spotify playlist of most of
them, but not all. The list is inline below as well, with many (but not all)
tracks linking to Bandcamp, if I could find them there.
This is a bit late, sorry. If anyone listens to something here and has any
feedback I'd love to hear it.
(If you are reading this on an aggregation site, it's possible the embeds won't
work. If so, click through to my main site)
Spotify playlist: https://open.spotify.com/playlist/3bEvEguRnf9U1RFrNbv5fk?si=9084cbf78c364ac8;
The list, with Bandcamp embeds where possible:
I hope you had a nice Halloween!
I've collected together some songs that I've enjoyed over the last couple of
years that loosely fit a theme: ambient, instrumental, experimental, industrial,
dark, disconcerting, etc. I've prepared a Spotify playlist of most of
them, but not all. The list is inline below as well, with many (but not all)
tracks linking to Bandcamp, if I could find them there.
This is a bit late, sorry. If anyone listens to something here and has any
feedback I'd love to hear it.
(If you are reading this on an aggregation site, it's possible the embeds won't
work. If so, click through to my main site)
Spotify playlist: https://open.spotify.com/playlist/3bEvEguRnf9U1RFrNbv5fk?si=9084cbf78c364ac8;
The list, with Bandcamp embeds where possible:









 youngest LUKS user I know...
So I'm in Berlin currently to attend the fourth
youngest LUKS user I know...
So I'm in Berlin currently to attend the fourth 







 Almost 2 decades ago,
Almost 2 decades ago, 









 I wanted to understand how kids between 10 and 18 conceive the internet.
Surely, we have seen a generation that we call digital natives grow up with
the internet. Now, there is a younger generation who grows up with pervasive
technology, such as smartphones, smart watches, virtual assistants and so on.
And only a few of them have parents who work in IT or engineering
I wanted to understand how kids between 10 and 18 conceive the internet.
Surely, we have seen a generation that we call digital natives grow up with
the internet. Now, there is a younger generation who grows up with pervasive
technology, such as smartphones, smart watches, virtual assistants and so on.
And only a few of them have parents who work in IT or engineering
 The youngest respondent, a 9 year old girl, drew a screen with lots of people
around it and the words film, series, network, video , as well as a play
icon. She said that she mostly uses the internet to watch movies. She was the
only one who used a shared tablet and smartphone that belonged to her family,
not to herself. And she would explain the net like this to an alien:
The youngest respondent, a 9 year old girl, drew a screen with lots of people
around it and the words film, series, network, video , as well as a play
icon. She said that she mostly uses the internet to watch movies. She was the
only one who used a shared tablet and smartphone that belonged to her family,
not to herself. And she would explain the net like this to an alien:
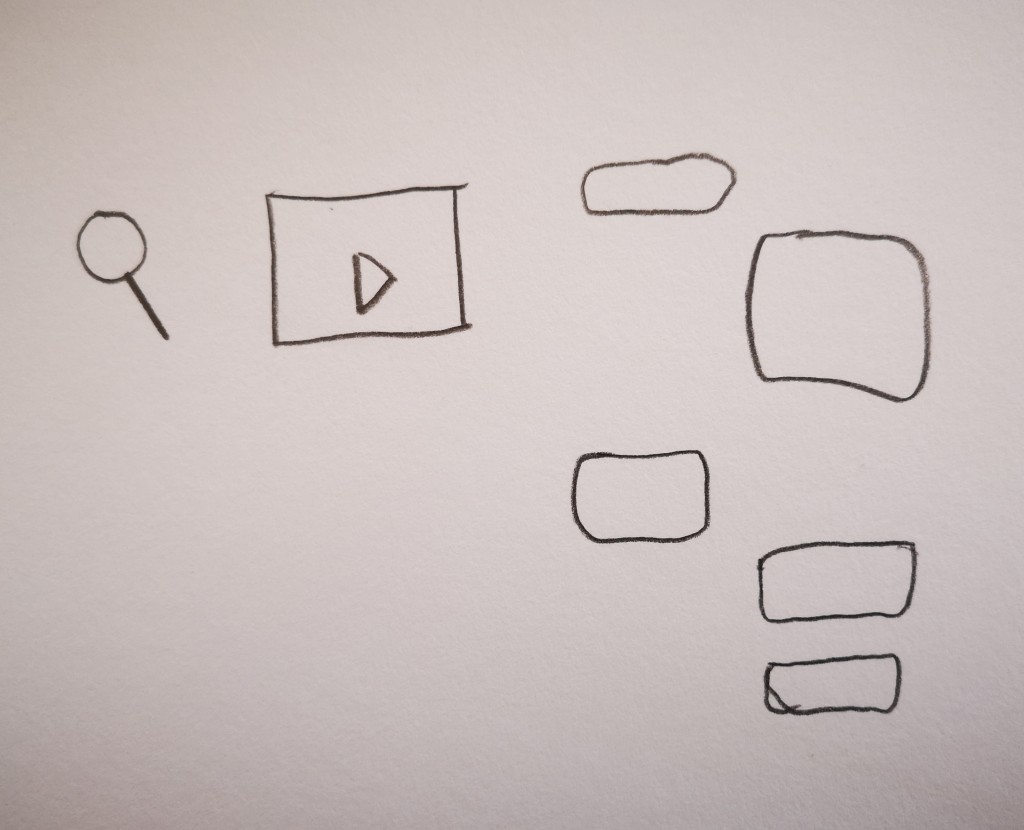 A 10 year old boy represented the internet by recalling user interface
elements he sees every day in his drawing: a magnifying glass (search
engine), a play icon (video streaming), speech bubbles (instant
messaging). He would explain the internet like this to an alien:
A 10 year old boy represented the internet by recalling user interface
elements he sees every day in his drawing: a magnifying glass (search
engine), a play icon (video streaming), speech bubbles (instant
messaging). He would explain the internet like this to an alien:
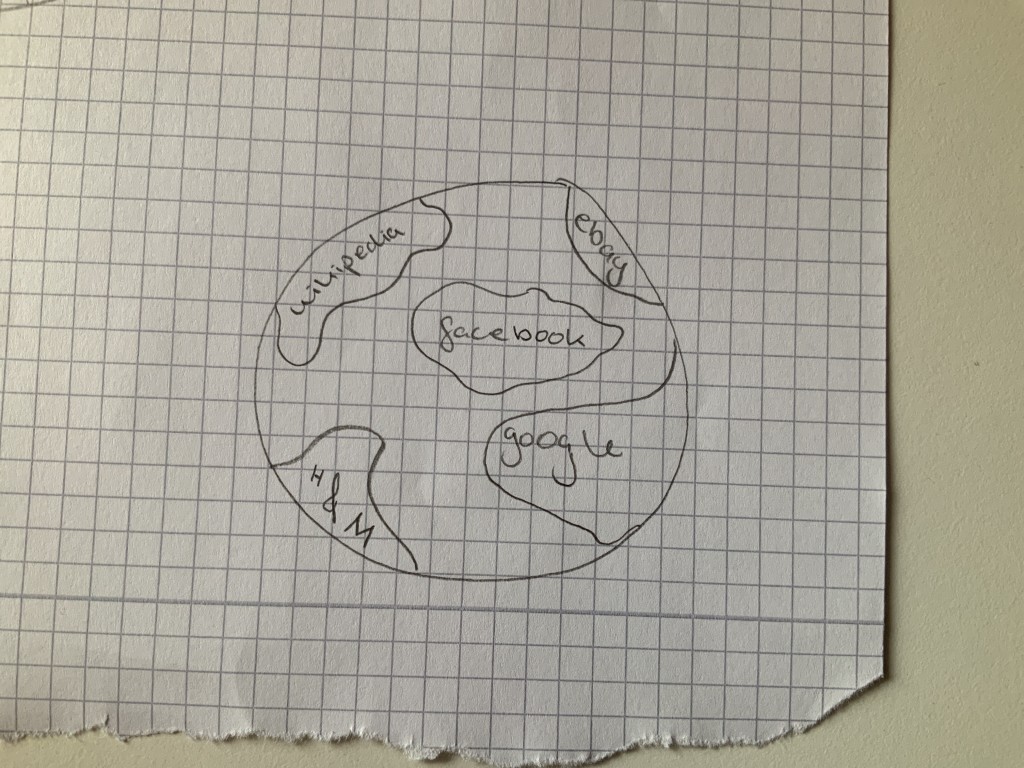 A 12 year old girl imagines the internet like a second, intangible, planet
where Google, Wikipedia, Facebook, Ebay, or H&M are continents that one enters
into.
A 12 year old girl imagines the internet like a second, intangible, planet
where Google, Wikipedia, Facebook, Ebay, or H&M are continents that one enters
into.
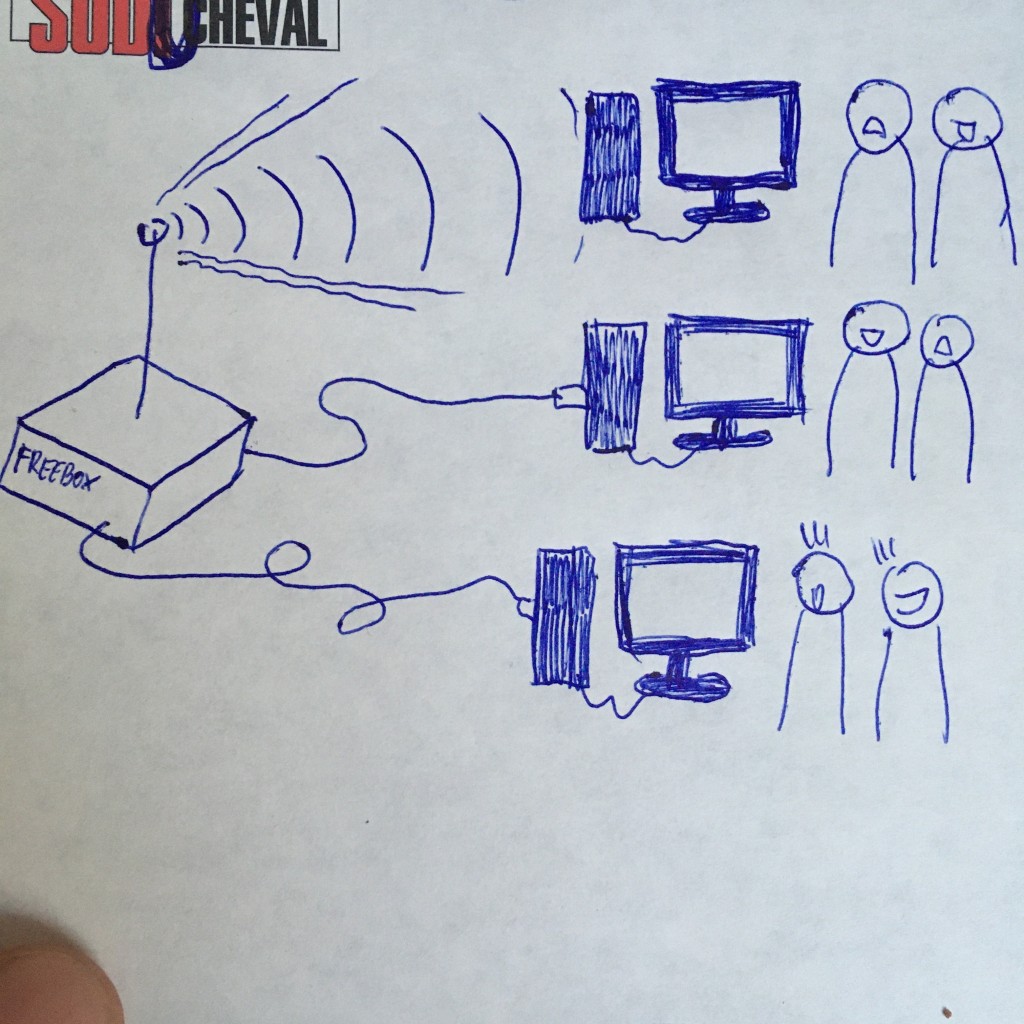 A 15 year old boy knew that his family s devices are connected to a home router
(Freebox is a router from the French ISP Free) but lacked an imagination of the
rest of the internet s functioning. When I asked him about what would be behind
the router, on the other side, he said what s behind is like a black hole to
him. However, he was the only interviewee who did actually draw cables, wifi
waves, a router, and the local network. His drawing is even extremely precise,
it just lacks the cable connecting the router to the rest of the internet.
A 15 year old boy knew that his family s devices are connected to a home router
(Freebox is a router from the French ISP Free) but lacked an imagination of the
rest of the internet s functioning. When I asked him about what would be behind
the router, on the other side, he said what s behind is like a black hole to
him. However, he was the only interviewee who did actually draw cables, wifi
waves, a router, and the local network. His drawing is even extremely precise,
it just lacks the cable connecting the router to the rest of the internet.
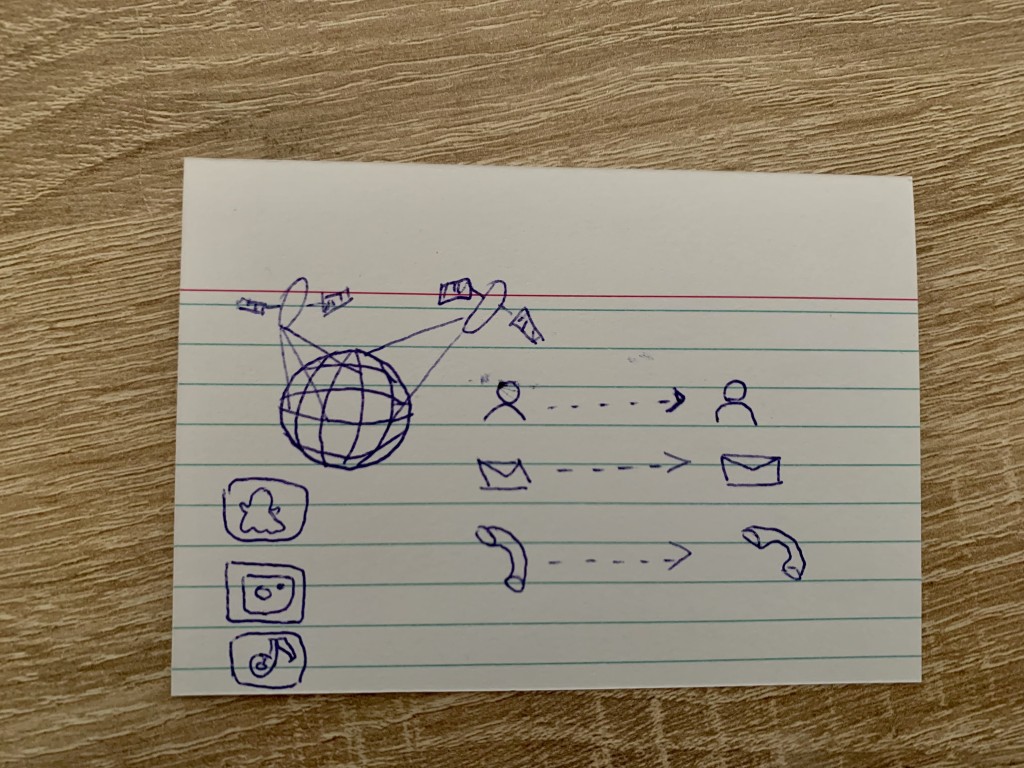 A 17 year old girl would explain the internet to an alien as follows:
A 17 year old girl would explain the internet to an alien as follows:










